- Published on
Asus Vivobook X15
Preface
This post is mostly a rant about how I discovered a potential firmware security vulnerability in my newest laptop and how I dealt with it.
Asus Vivobook X15
Earlier this year I got myself a new laptop — an Asus Vivobook X15. It's a surprisingly powerful laptop with a 12th-generation Intel processor, priced at around 900 EUR.
Laptop specifications
| Component | Specification |
|---|---|
| Processor | Intel Core i5 12500H Alder Lake, 4.50 GHz (18 MB Cache) Performance Cores: 4 Cores, 8 Threads, 2.5 GHz Base, 4.5 GHz Turbo Efficient Cores: 8 Cores, 8 Threads, 3.3 GHz Turbo |
| Operating System | Windows 11 Home |
| Memory (RAM) | 8GB DDR4 on board 8GB DDR4 SO-DIMM (I had to buy and install this one though) |
| Storage | 512GB M.2 NVMe PCIe 3.0 SSD |
| Graphics | Intel UHD / Intel Iris Xe 80EU (when in dual channel mode) |
| Display | 15.6-inch 2.8K (2880 x 1620) OLED 16:9 aspect ratio 0.2ms response time 120Hz refresh rate |
CPU
See how this laptop's CPU compares against other ones commonly used in laptops:

Its single-thread performance:

I was delighted with this little CPU.
This laptop was intended to be a replacement for my similarly priced, 12-and-a-half-year-old desktop PC, which I turned into a NAS (that's a whole other post). I'm not going to compare the performance between the two since more than a decade of innovations render almost every component obsolete by default. The CPU alone is at least 89.90% faster.
GPU
There's no dedicated GPU in the model that I own (there are other models). With dual channel memory, you can unlock Iris Xe, which is good enough for light gaming (it can use up to 50% of system RAM for itself though). It can even run some modern-ish games at 720p.1 Without RAM in dual channel mode, you would have to stick with the slower Intel UHD which has only 128 MB of memory.2
Firmware security
I've been learning about firmware security and side-channel attacks on computers and smartphones since 2014. There have been many impressive vulnerabilities discovered over the years, especially in x86-based platforms. Some of the notable ones were in Intel Management Engine, which has been part of virtually all Intel platforms since 2008. It's a secondary system that is running its own OS based on MINIX3, with special access to network interface and memory. Its main purpose is out-of-band remote management in an enterprise setting, DRM (secure video path) and more.
The Intel Management Engine is a proprietary, mostly undocumented, firmware system that provides many extraneous features that are generally not usable or useful to our users, with multiple known vulnerabilities that compromise the entire system.4
Regular users, however, will have to use the computers with these extraneous features, which had several critical vulnerabilities in it in the past, with no way to disable them. I was curious whether my Vivobook X15 is also vulnerable, so I decided to scan it with Intel® Converged Security and Management Engine Version Detection Tool:

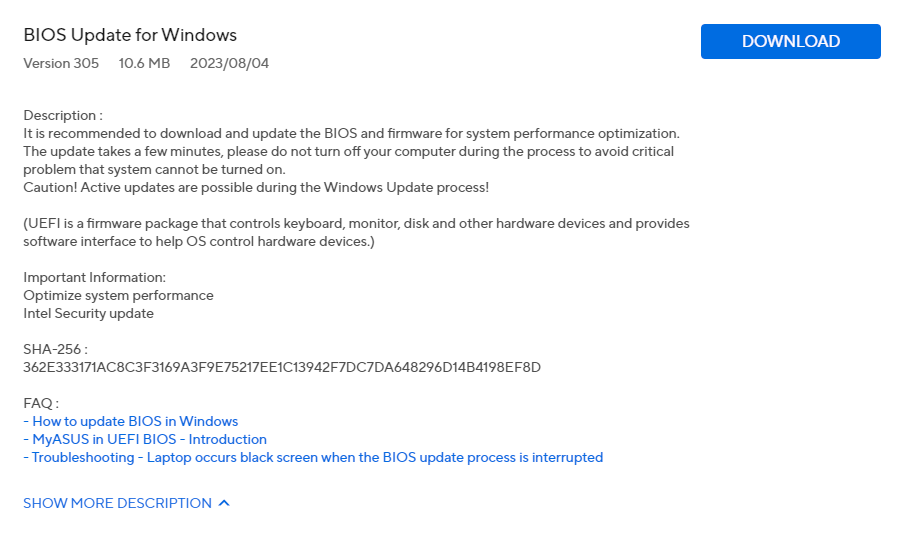
It may be a false positive since the tool is a bit outdated, but just to be sure, I reached out to Asus support in April this year, and they responded by saying that they will address it in the next BIOS update. About 3 months later, a new version 305 was released, which I installed.
I ran the Intel CSME tool again and it still reported that the machine is vulnerable, so I contacted Asus support again. They replied two days later saying that this would be fixed in the next BIOS version 306, which I'm still awaiting. I'll update this post once it's released.
Conclusions
There are numerous initiatives (including Google's5) working on disabling and removing Intel ME. You can try flashing custom BIOS like coreboot or libreboot with disabled Intel ME firmware blobs, but keep in mind that not every motherboard is supported. Back in 2018, I flashed locally built coreboot binary with Raspberry Pi and flashrom on my ThinkPad T420 where I now run Qubes OS which enables further mitigations on known vulnerabilities by disabling certain CPU features.
You can also try to switch to AMD, although there's an equivalent of Intel ME which is called AMD PSP (albeit less powerful/vulnerable).
Update (28-01-2024)
Looks like this issue has been fixed in BIOS version 306. I've updated my laptop and the latest Intel CSME tool (version 9.0.3.0) no longer reports any vulnerabilities.

Footnotes
https://www.youtube.com/watch?v=084Ez5EXWMU "Intel Iris Xe Gaming (31 games)" ↩
https://www.linkedin.com/pulse/intel-iris-xe-graphics-mystery-conrad-h-blickenstorfer "The Intel Iris Xe Graphics mystery" ↩
https://www.bleepingcomputer.com/news/hardware/intels-secret-cpu-on-chip-management-engine-me-runs-on-minix-os/ "Intel's Secret CPU-On-Chip Management Engine (ME) Runs on MINIX OS" ↩
https://support.system76.com/articles/intel-me/#what-is-the-intel-management-engine "What is the Intel Management Engine? (System76)" ↩
https://www.tomshardware.com/news/google-removing-minix-management-engine-intel,35876.html "Google Working To Remove MINIX-Based ME From Intel Platforms" ↩